Boom Gate Access Control System: Enhancing Security and Efficiency
In today’s fast-paced world, security is a top concern for businesses, residential complexes, parking lots, and various other facilities. One effective solution that has gained popularity is the boom gate access control system. This system provides a secure and efficient way to manage vehicle entry and exit points.
A boom gate access control system consists of a sturdy barrier arm (boom gate) that can be raised or lowered to control the flow of vehicles. It is typically installed at entrances or exits to restrict unauthorized access and ensure only authorized vehicles are granted entry.
Enhanced Security:
The primary purpose of a boom gate access control system is to enhance security. By installing this system, you can effectively prevent unauthorized vehicles from entering your premises. This helps in maintaining the safety and privacy of your property. With advanced features such as RFID card readers or biometric scanners, only authorized personnel can gain access through the boom gate.
Efficient Traffic Management:
Apart from security benefits, a boom gate access control system also offers efficient traffic management. The automated barrier arm ensures smooth and organized vehicle flow by allowing one vehicle to pass at a time. This prevents congestion and reduces the chances of accidents or collisions at entry or exit points.
Integration with Other Systems:
Modern boom gate access control systems can be seamlessly integrated with other security systems such as CCTV cameras, license plate recognition systems (ANPR), or attendance management software. This integration allows for better monitoring and tracking of vehicles entering or exiting the premises. It also enables you to generate detailed reports on vehicle movements for auditing purposes.
Customizable Access Permissions:
One of the key advantages of a boom gate access control system is its ability to provide customizable access permissions. You can set different levels of authorization for various individuals or groups based on their roles or requirements. For example, employees may have unrestricted access during working hours while visitors may be granted limited access for specific time periods. This flexibility ensures that only authorized vehicles are allowed entry, improving overall security.
Remote Monitoring and Control:
With the advancement of technology, many boom gate access control systems now offer remote monitoring and control capabilities. This means that you can manage and monitor the system from a centralized location or even through a mobile application. Remote access allows you to open or close the boom gate, grant access to visitors, or receive real-time notifications of any security breaches. This feature offers convenience and added security for facility managers or security personnel.
In conclusion, a boom gate access control system is an effective solution for enhancing security and managing vehicle flow at entry and exit points. It provides a secure and efficient way to control access to your premises while offering customization options, integration with other systems, and remote monitoring capabilities. By implementing this system, you can ensure the safety of your property, streamline traffic management, and enjoy peace of mind knowing that unauthorized vehicles are kept at bay.
9 Essential Tips for Boom Gate Access Control System Management
- Make sure to have the right personnel trained in operating the boom gate access control system.
- Ensure that all users of the system have the necessary authorization and credentials to use it.
- Regularly inspect and maintain all components of the system, such as sensors, cameras, and card readers.
- Establish a backup plan in case of power outages or other technical difficulties with your access control system.
- Set up an alarm system to alert you if someone attempts unauthorized entry into your facility through the boom gate access control system.
- Use a secure authentication method for user identification, such as biometric scanning or two-factor authentication (e.g., password and PIN).
- Utilize software updates regularly to ensure that your boom gate access control system is up-to-date with security patches and bug fixes for optimal performance and security measures against hackers or malware attacks on your networked systems or data centers associated with it .
- Establish clear policies about who is allowed to enter certain areas within your facility using this type of access control technology so everyone is aware of their responsibilities when using it .
- Monitor usage patterns on a regular basis to detect any suspicious activity or potential threats related to unauthorized entry attempts through this type of security measure .
Make sure to have the right personnel trained in operating the boom gate access control system.
Make the Most of Your Boom Gate Access Control System: Ensure Proper Training for Personnel
Investing in a boom gate access control system is a wise decision to enhance security and streamline vehicle management at your premises. However, it is equally crucial to ensure that the right personnel are trained in operating this system effectively. Proper training plays a vital role in maximizing the benefits of your access control system and maintaining its smooth operation.
Why is training important?
Operating a boom gate access control system requires technical knowledge and familiarity with its functionalities. By providing proper training to your personnel, you equip them with the necessary skills to handle the system efficiently. This ensures that they can carry out daily operations, such as granting access or troubleshooting minor issues, without any hiccups.
Efficient System Management:
A well-trained operator can navigate through the various features and settings of the boom gate access control system effortlessly. They will be able to handle routine tasks such as adding or removing authorized users, adjusting access permissions, and generating reports accurately and efficiently. This not only saves time but also ensures that the system operates smoothly, minimizing disruptions or errors.
Quick Troubleshooting:
Even with advanced technology, occasional glitches or technical issues may arise in any system. Having personnel trained in operating the boom gate access control system allows for quick troubleshooting when problems occur. They will be able to identify and resolve minor issues promptly, reducing downtime and ensuring continuous operation of the system.
Enhanced Security:
Properly trained personnel play a crucial role in maintaining security levels provided by your boom gate access control system. They are responsible for verifying credentials, monitoring entry/exit points, and ensuring only authorized vehicles gain access. With comprehensive training on security protocols and best practices, they can effectively manage potential security threats or breaches.
Safety Measures:
In addition to security considerations, trained personnel are also aware of safety measures associated with operating a boom gate access control system. They understand how to handle emergency situations, such as power outages or system malfunctions, without compromising the safety of individuals or vehicles. Their knowledge and expertise contribute to a safe and secure environment for all stakeholders.
Regular Updates and Skill Enhancement:
As technology evolves, updates and enhancements to the boom gate access control system may become available. Trained personnel are better equipped to adapt to these changes and utilize new features effectively. By staying up-to-date with the latest advancements, they can optimize the performance of the system and make informed decisions regarding its operation.
In conclusion, ensuring that the right personnel are trained in operating your boom gate access control system is vital for maximizing its benefits. Proper training enhances system management, enables quick troubleshooting, strengthens security measures, promotes safety protocols, and facilitates adaptation to new technologies. By investing in training programs for your personnel, you can harness the full potential of your access control system and maintain a secure environment for your premises.
Ensure that all users of the system have the necessary authorization and credentials to use it.
Ensuring Authorized Access: Key to Effective Boom Gate Access Control System
When it comes to implementing a boom gate access control system, one crucial tip that cannot be overlooked is to ensure that all users of the system have the necessary authorization and credentials to use it. This simple yet essential practice plays a significant role in maintaining the security and effectiveness of the system.
Unauthorized access can pose serious risks and compromise the entire purpose of having a boom gate access control system in place. Therefore, it is imperative to establish strict protocols and procedures for granting access permissions. Here are a few reasons why this tip is vital:
Security Enhancement:
By ensuring that only authorized individuals have access to the boom gate control system, you significantly enhance security levels. Unauthorized users may attempt to gain entry or manipulate the system, which can lead to potential breaches or vulnerabilities. By strictly adhering to authorization protocols, you minimize the risk of unauthorized access and maintain a secure environment.
Preventing Misuse:
Unauthorized or untrained individuals using the boom gate control system can lead to misuse or mishandling of the equipment. This can result in accidents, damage to vehicles or property, or disruption in traffic flow. By verifying credentials and authorizations before granting access, you prevent such incidents from occurring.
Accountability and Audit Trails:
Having a well-defined authorization process ensures accountability for any actions taken within the boom gate control system. Each user’s credentials are logged, allowing for accurate tracking and auditing if any security breaches occur or if there is a need for investigation in case of an incident.
System Efficiency:
Allowing only authorized personnel who are trained on operating the boom gate control system ensures its efficient use. Users with proper credentials will be familiar with its functionalities, reducing errors or delays during operation. This promotes smooth traffic flow at entry and exit points while maintaining security standards.
To implement this tip effectively:
– Establish clear guidelines for granting authorization and credentials.
– Conduct thorough background checks and verifications before providing access.
– Regularly review and update the authorization list to ensure it remains up to date.
– Provide proper training to authorized users on system operation, safety protocols, and emergency procedures.
– Implement a robust access control management system that allows for easy administration of user credentials.
In conclusion, ensuring that all users of the boom gate access control system have the necessary authorization and credentials is crucial for maintaining security, preventing misuse, promoting efficiency, and establishing accountability. By following this tip diligently, you can maximize the effectiveness of your boom gate access control system while safeguarding your premises and providing a secure environment for all.
Regularly inspect and maintain all components of the system, such as sensors, cameras, and card readers.
Regular Inspection and Maintenance: Key to a Reliable Boom Gate Access Control System
A boom gate access control system is a valuable tool for enhancing security and managing vehicle flow at entrances and exits. To ensure its optimal performance, it is crucial to regularly inspect and maintain all components of the system, including sensors, cameras, and card readers. This proactive approach helps in identifying any potential issues and ensures that the system operates smoothly at all times.
Sensors play a vital role in detecting the presence of vehicles and triggering the boom gate to open or close. Regularly inspecting these sensors ensures that they are clean, properly aligned, and free from any obstructions such as dirt or debris. By doing so, you can avoid false readings or malfunctions that may disrupt the flow of vehicles or compromise security.
Cameras are another critical component of a boom gate access control system. They enable visual monitoring of vehicles entering or exiting the premises. Regular inspection of cameras ensures that they are clean, focused correctly, and providing clear images. It is also important to check camera connections and cables to ensure uninterrupted transmission of video footage.
Card readers are commonly used for granting access to authorized personnel through RFID cards or other identification methods. These card readers should be inspected regularly to ensure they are functioning correctly. Check for any signs of wear or damage on the card reader surface as well as the card itself. Additionally, ensure that the card reader is properly calibrated to read cards accurately.
In addition to regular inspections, it is essential to schedule routine maintenance for your boom gate access control system. This may involve cleaning components, lubricating moving parts, checking electrical connections, updating software/firmware if applicable, and conducting performance tests.
By following a comprehensive maintenance plan, you can identify potential issues early on and address them promptly. This proactive approach helps prevent unexpected breakdowns or malfunctions that could compromise security or cause inconvenience for users.
Remember that maintenance should be performed by trained professionals or technicians with expertise in access control systems. They have the knowledge and tools to conduct thorough inspections, identify problems, and perform necessary repairs or replacements.
In conclusion, regularly inspecting and maintaining all components of a boom gate access control system is crucial for its reliable operation. By keeping sensors, cameras, and card readers in optimal condition, you can ensure a smooth flow of vehicles, accurate identification of authorized personnel, and enhanced security at your premises. Invest in regular maintenance to prolong the lifespan of your system and enjoy its benefits for years to come.
Establish a backup plan in case of power outages or other technical difficulties with your access control system.
Establishing a Backup Plan for Unforeseen Events in Boom Gate Access Control Systems
When it comes to the security and efficiency of your premises, a boom gate access control system can be an invaluable asset. However, it is essential to be prepared for unforeseen events such as power outages or technical difficulties that may disrupt the functioning of your access control system. To ensure uninterrupted operation and maintain security, it is crucial to establish a backup plan.
Power outages can occur unexpectedly, and without a backup plan, your access control system may become non-functional, leaving your premises vulnerable. Here are some key considerations to establish an effective backup plan:
Uninterruptible Power Supply (UPS):
Invest in a reliable uninterruptible power supply (UPS) system that can provide temporary power during outages. A UPS acts as a backup power source and ensures that critical components of your access control system, including the boom gate, continue to function until power is restored.
Backup Power Generator:
For longer power outages or situations where extended backup power is required, consider installing a backup power generator. A generator can provide continuous electricity supply to your access control system and other essential equipment during extended periods without utility power.
Manual Override Mechanism:
Incorporate a manual override mechanism into your boom gate access control system design. This allows authorized personnel to manually operate the boom gate in case of technical difficulties or complete power failure. Ensure that relevant staff members are trained on how to use the manual override mechanism effectively.
Regular Maintenance and Testing:
Regularly maintain and test your backup systems to ensure they are in optimal working condition when needed. Schedule routine inspections of the UPS, generator, and manual override mechanism to identify any potential issues beforehand.
Communication Plan:
Establish clear communication protocols within your organization in case of emergencies or technical difficulties with the access control system. Designate specific personnel responsible for coordinating alternative security measures during downtime, such as deploying additional security staff or implementing manual access control procedures.
By implementing a well-thought-out backup plan, you can minimize the impact of power outages or technical difficulties on your boom gate access control system. This ensures that your premises remain secure and operational even during unforeseen events. Remember to regularly review and update your backup plan to adapt to any changes in your access control system or facility requirements.
Investing time and resources into establishing a robust backup plan demonstrates your commitment to maintaining the security and efficiency of your premises, providing peace of mind for both you and those who rely on the access control system for safe entry and exit.
Set up an alarm system to alert you if someone attempts unauthorized entry into your facility through the boom gate access control system.
Secure Your Premises with an Alarm System for Boom Gate Access Control
When it comes to ensuring the security of your facility, every measure counts. One valuable tip for maximizing the effectiveness of your boom gate access control system is to set up an alarm system that alerts you in case of any unauthorized entry attempts.
While a boom gate access control system itself acts as a strong deterrent against unauthorized access, adding an alarm system takes security to the next level. Here’s why:
Immediate Alert:
By integrating an alarm system with your boom gate access control, you create a proactive security solution. In the event of someone attempting unauthorized entry through the boom gate, the alarm system will immediately trigger an alert. This prompt notification allows you or your security personnel to respond swiftly and take necessary action.
Prevention and Deterrence:
An alarm system not only alerts you but also acts as a powerful deterrent against potential intruders. The loud siren or sound signal can startle and discourage unauthorized individuals from proceeding any further into your facility. This added layer of security helps prevent incidents before they even occur.
Enhanced Monitoring:
With an alarm system in place, you gain enhanced monitoring capabilities for your boom gate access control. For instance, if someone tries to tamper with or force open the boom gate, sensors connected to the alarm system will detect such activity and trigger an immediate alert. This allows you to monitor and respond to any suspicious behavior promptly.
Integration with Security Systems:
Modern alarm systems can be seamlessly integrated with other security systems, such as CCTV cameras or motion sensors. This integration provides comprehensive surveillance coverage around the boom gate area. If an unauthorized entry attempt is detected by these additional security measures, the alarm will activate simultaneously, providing multiple layers of protection.
Customized Alerts:
Alarm systems offer flexibility in setting up customized alerts based on different scenarios. For example, you can configure distinct notifications for different types of breaches—whether it’s attempted forced entry, tailgating, or a certain number of failed access attempts. This customization ensures you receive specific information about the nature of the security breach.
Peace of Mind:
By setting up an alarm system for your boom gate access control, you gain peace of mind knowing that you have an extra layer of protection in place. The system works tirelessly to keep your facility secure and promptly notifies you of any unauthorized access attempts. This allows you to maintain a proactive approach towards security and protect your assets effectively.
In conclusion, integrating an alarm system with your boom gate access control system is a valuable tip for enhancing the security of your facility. It provides immediate alerts, acts as a deterrent, enhances monitoring capabilities, integrates with other security systems, offers customized alerts, and ultimately brings peace of mind. By implementing this tip, you can ensure that your premises remain secure and well-protected against unauthorized access through the boom gate.
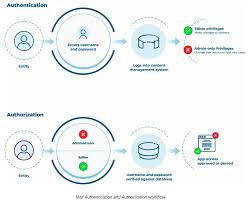
Use a secure authentication method for user identification, such as biometric scanning or two-factor authentication (e.g., password and PIN).
Enhancing Security with Secure Authentication Methods in Boom Gate Access Control Systems
In the realm of boom gate access control systems, ensuring the utmost security is paramount. One crucial tip to achieve this is by implementing a secure authentication method for user identification. By incorporating robust authentication measures such as biometric scanning or two-factor authentication (2FA), such as a combination of password and PIN, you can significantly enhance the security of your access control system.
Biometric scanning, a cutting-edge technology, utilizes unique physical or behavioral characteristics to identify individuals accurately. This method often includes fingerprint recognition, facial recognition, or iris scanning. By employing biometric scanning as an authentication method, you can ensure that only authorized personnel with registered biometric data gain access through the boom gate. This eliminates the risk of unauthorized entry through stolen access cards or PINs.
Another effective approach is implementing two-factor authentication (2FA). With 2FA, users are required to provide two different types of credentials for verification before accessing the premises. Typically, this involves combining something the user knows (e.g., a password) with something they possess (e.g., a PIN generated by an authenticator app). This double-layered security significantly reduces the chances of unauthorized access even if one factor is compromised.
By incorporating these secure authentication methods into your boom gate access control system, you can enjoy several benefits:
- Heightened Security: Biometric scanning and 2FA add an extra layer of security by ensuring that only authorized individuals can gain entry. This minimizes the risk of unauthorized personnel infiltrating restricted areas.
- Elimination of Credential Sharing: Biometric data and personalized credentials cannot be easily shared or replicated like traditional access cards or passwords. This prevents unauthorized individuals from using someone else’s credentials to gain entry.
- Enhanced Accountability: Secure authentication methods leave behind an auditable trail that helps track and monitor who accessed specific areas and at what time. In case of any security breaches or incidents, this information can prove invaluable for investigations.
- Convenience and User-Friendliness: Biometric scanning eliminates the need to carry access cards or remember complex passwords, making it a convenient and user-friendly authentication method. Similarly, 2FA provides an additional layer of security without adding excessive complexity to the user experience.
Implementing secure authentication methods in your boom gate access control system demonstrates your commitment to safeguarding your premises and assets. By utilizing biometric scanning or two-factor authentication, you can enhance security, deter unauthorized access attempts, and ensure that only authorized personnel gain entry through the boom gate.
Utilize software updates regularly to ensure that your boom gate access control system is up-to-date with security patches and bug fixes for optimal performance and security measures against hackers or malware attacks on your networked systems or data centers associated with it .
Keeping Your Boom Gate Access Control System Secure: The Importance of Regular Software Updates
In today’s digital age, where technology is constantly evolving, it is crucial to prioritize the security of your boom gate access control system. One effective way to ensure optimal performance and protect against potential security threats is by regularly utilizing software updates.
Software updates play a vital role in keeping your system up-to-date with the latest security patches and bug fixes. These updates are designed to address vulnerabilities that may have been discovered since the initial installation of your access control system. By promptly installing these updates, you can significantly reduce the risk of hackers or malware attacks on your networked systems or data centers associated with it.
Here are a few reasons why regular software updates are essential for maintaining the security and performance of your boom gate access control system:
- Enhanced Security: Software updates often include critical security patches that address known vulnerabilities or weaknesses in the system. By installing these updates, you strengthen your defense against potential threats and ensure that unauthorized individuals cannot exploit any loopholes in your access control system.
- Bug Fixes: Just like any other software, access control systems may encounter bugs or glitches that can impact their functionality. Regular software updates help identify and fix these issues, ensuring smooth operation and minimizing any disruptions caused by technical errors.
- Compatibility: With advancements in technology, it is common for new devices or components to be introduced into the market. Software updates often include compatibility enhancements that allow your boom gate access control system to seamlessly integrate with newer devices or technologies. This ensures that you can take advantage of the latest features and functionalities available.
- Performance Optimization: Software updates not only focus on security but also aim to improve overall performance. By installing these updates, you can experience enhanced speed, efficiency, and stability in your access control system’s operations.
To make the most out of software updates for your boom gate access control system, consider implementing the following practices:
– Regularly check for updates: Stay proactive by checking for software updates provided by the manufacturer or service provider. They may release updates periodically to address security concerns or introduce new features.
– Schedule regular maintenance: Set up a maintenance schedule to ensure that software updates are installed promptly. This can be done during non-peak hours to minimize any potential disruptions to your operations.
– Backup system configurations: Before installing any software updates, it is advisable to back up your system configurations. This precautionary step ensures that you can revert to a previous state if any unforeseen issues arise during the update process.
In conclusion, keeping your boom gate access control system secure is of utmost importance in today’s digital landscape. Regularly utilizing software updates helps ensure that your system remains up-to-date with the latest security measures and performance enhancements. By staying proactive and implementing these practices, you can enhance the overall security and functionality of your access control system, providing peace of mind for both you and your users.
Establish clear policies about who is allowed to enter certain areas within your facility using this type of access control technology so everyone is aware of their responsibilities when using it .
Establish Clear Policies for Effective Boom Gate Access Control
Implementing a boom gate access control system is a smart move to enhance security and streamline access within your facility. However, to ensure its effectiveness, it is crucial to establish clear policies regarding who is allowed to enter specific areas using this technology. By doing so, you can create a secure environment and ensure that everyone understands their responsibilities when utilizing the system.
Clear policies play a vital role in maintaining order and security within your facility. When implementing a boom gate access control system, it is essential to define and communicate the access permissions clearly. Determine which individuals or groups are authorized to enter specific areas and at what times. This could include employees, visitors, contractors, or any other relevant stakeholders.
By establishing these policies, you create awareness among all individuals accessing your facility. They will understand the boundaries and limitations associated with the boom gate access control system. This clarity helps prevent unauthorized access attempts and minimizes confusion among users.
To effectively communicate these policies:
- Inform all stakeholders: Ensure that all employees, visitors, and relevant personnel are aware of the policies regarding the use of the boom gate access control system. Conduct training sessions or orientation programs to familiarize them with the technology and its associated rules.
- Display clear signage: Install visible signs near entry points indicating who is allowed entry into specific areas. These signs should be easily readable and provide concise instructions on how to use the boom gate system correctly.
- Provide written guidelines: Create written guidelines or handbooks outlining the policies related to accessing different areas within your facility using the boom gate access control system. Distribute these guidelines to all authorized users so they can refer to them whenever needed.
- Regularly review and update policies: As your facility evolves or personnel changes occur, it’s important to review and update your access control policies accordingly. Keep track of any modifications in personnel roles or departments that may affect their access permissions.
By establishing clear policies and consistently enforcing them, you create a culture of accountability and responsibility among all individuals using the boom gate access control system. This not only enhances security but also promotes a smooth and efficient flow of authorized personnel within your facility.
Remember, effective access control is not just about the technology itself; it’s about the policies and guidelines that govern its usage. By ensuring that everyone is aware of their responsibilities when using the boom gate access control system, you can maintain a secure environment while fostering a sense of trust and order within your facility.
Monitor usage patterns on a regular basis to detect any suspicious activity or potential threats related to unauthorized entry attempts through this type of security measure .
Monitoring Usage Patterns: Strengthening Security with Boom Gate Access Control Systems
When it comes to ensuring the utmost security for your premises, a boom gate access control system is an excellent choice. However, it’s important to go beyond just installing the system and take proactive measures to monitor its usage patterns regularly. By doing so, you can detect any suspicious activity or potential threats related to unauthorized entry attempts.
Regular monitoring of usage patterns allows you to stay one step ahead of potential security breaches. Here’s why it’s crucial:
- Identifying Suspicious Activity: By analyzing the data collected from your boom gate access control system, you can identify any unusual or suspicious patterns of entry attempts. For example, if there are repeated failed entry attempts by unauthorized individuals or if certain vehicles are consistently trying to gain access without proper authorization, these could be red flags indicating a potential security threat.
- Early Detection of Unauthorized Entry: Monitoring usage patterns helps in detecting any instances of unauthorized entry at the earliest stage possible. This allows you to take immediate action and prevent any further security breaches. By regularly reviewing access logs and comparing them with authorized personnel records, you can quickly identify any discrepancies and investigate them promptly.
- Enhancing Security Measures: Analyzing usage patterns enables you to assess the effectiveness of your existing security measures. If you notice any areas where vulnerabilities exist or where unauthorized entry attempts are more frequent, you can take corrective actions accordingly. This may involve strengthening physical barriers, updating access permissions, or implementing additional security features such as CCTV cameras or biometric scanners.
- Improving Access Control Policies: Monitoring usage patterns also helps in refining your access control policies. By understanding how people are utilizing the boom gate access control system, you can make informed decisions regarding access permissions and restrictions. For instance, if certain timeframes show higher incidences of unauthorized entry attempts, you may consider revising access hours or implementing stricter visitor management protocols during those periods.
- Preventing Potential Threats: Regular monitoring of usage patterns allows you to proactively identify potential threats before they escalate. By staying vigilant and detecting any suspicious activity or patterns, you can take preventive measures to mitigate the risks. This could involve notifying security personnel, implementing additional security measures, or conducting thorough investigations to uncover any underlying security loopholes.
In conclusion, monitoring usage patterns on a regular basis is crucial for maintaining the highest level of security with a boom gate access control system. It helps in identifying suspicious activity, detecting unauthorized entry attempts, enhancing overall security measures, improving access control policies, and preventing potential threats. By staying proactive and vigilant in monitoring your system’s usage patterns, you can ensure a safe and secure environment for your premises.